Verify Tapbit

How to Complete Identity Verification? A step-by-step guide
On this page, you can review your existing verification level, kindly fulfill the requirements for the corresponding Identity Verification level.
1. Log in to your Tapbit account and click [User Icon] - [ID Verification].
2. Select your country of residence and enter your personal information. Please ensure that your country of residence is consistent with your ID documents.
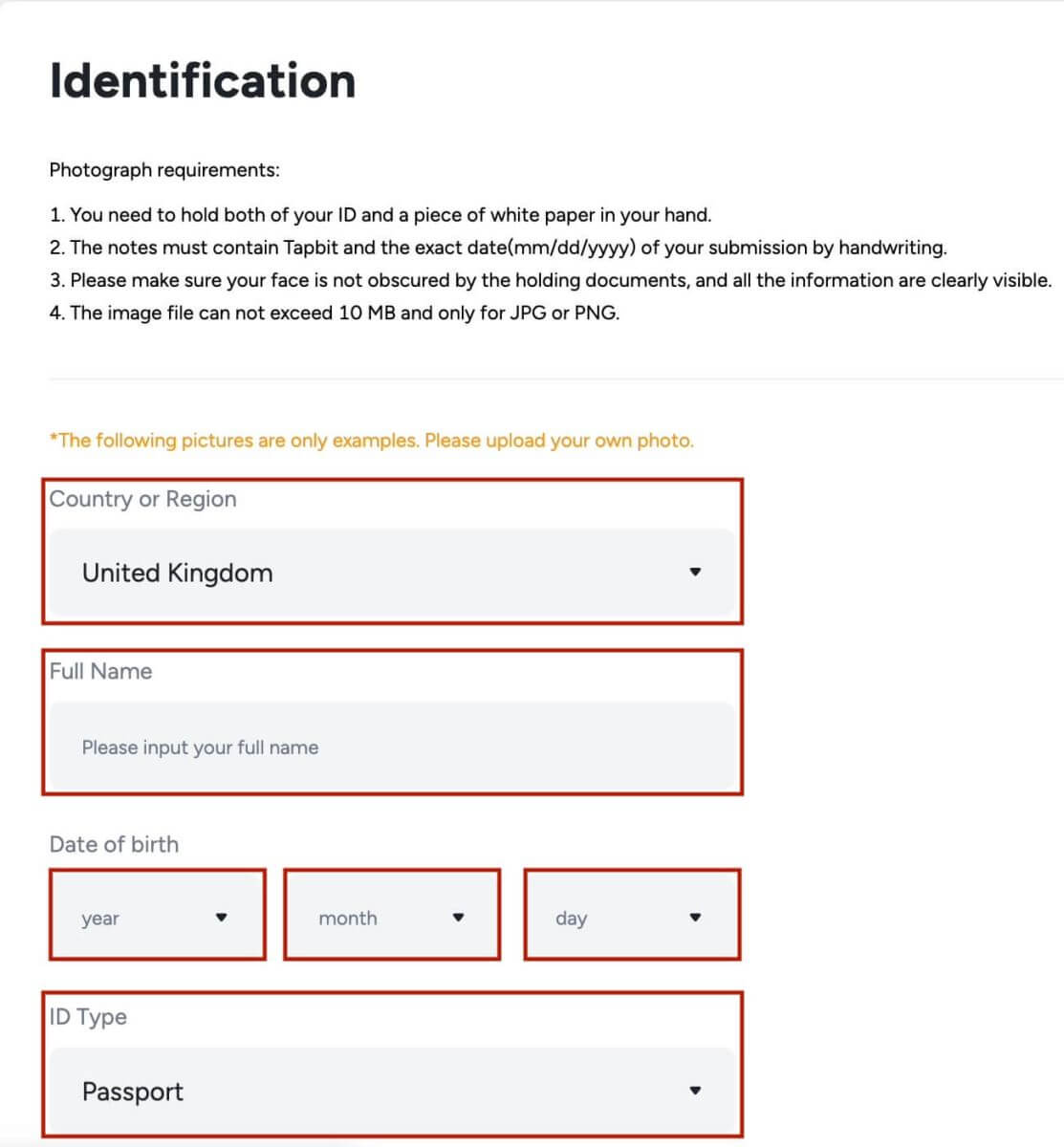
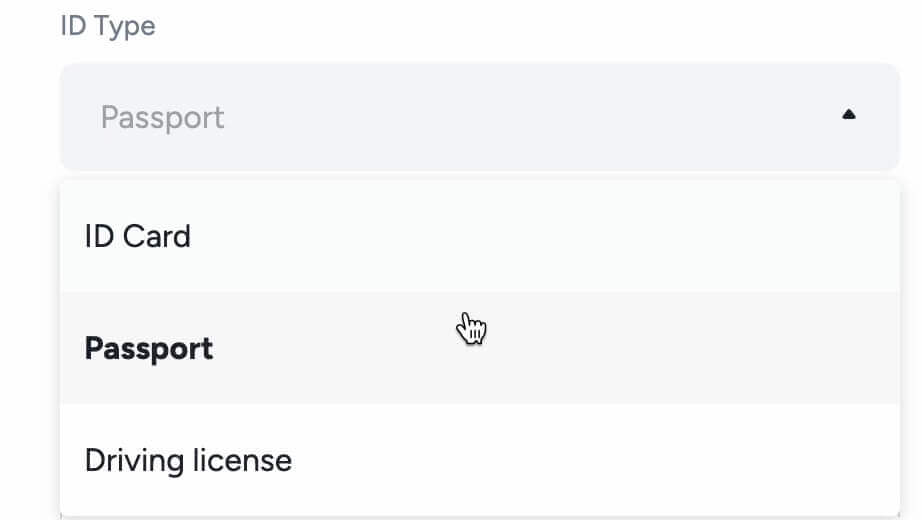
Please choose the type of ID and the country your documents were issued. Most users can choose to verify with a passport, ID card, or driver’s license. Please refer to the respective options offered for your country.
3. You will need to upload pictures of your ID documents.
4. You need to hold both your ID and a piece of paper with the notes in your hand, take a picture and upload. The notes must contain Tapbit and the exact date (mm/dd/yyyy) of your submission by handwriting.
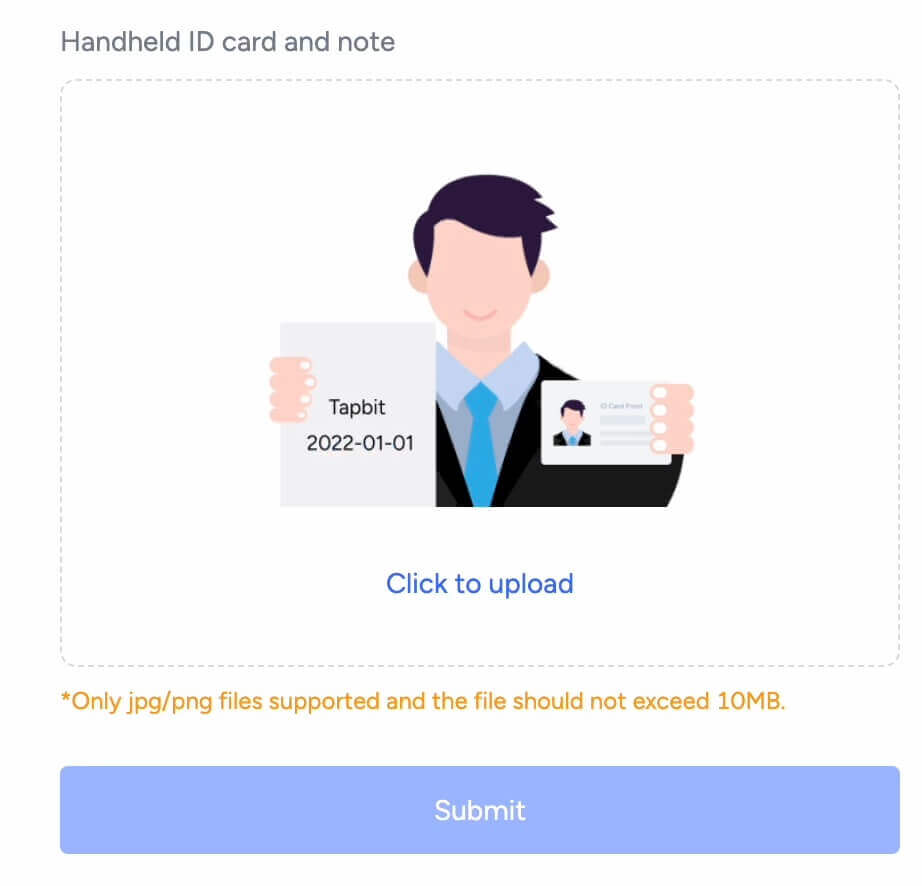
Please make sure your face is not obscured by the holding documents, and all the information is clearly visible.
5. After completing the process, please wait patiently. Tapbit will review your data in a timely manner. Once your application has been verified, they will send you an email notification.
How to secure your cryptocurrency exchange account on Tapbit
Step 1. Sign up for a new account on Tapbit
1. Visit the Tapbit website to access the homepage, then click on "Register" located in the upper right corner to proceed with the registration process.

2. Opt for either your email or mobile phone number to register, input the necessary details to finalize the registration, and set a secure password for your account.


3. Ensure that your password consists of 6–20 characters, including numbers. In this example, we are using an email address for the account creation.

4. Click on [Get the code], and you will receive a verification email from Tapbit at the provided email address. Check your email for the verification code and input it in the designated field.

5. Review the "TAPBIT Terms of Use" mark the checkbox for "I have read and agree" and then click on [Register] to successfully complete the registration process.

Sign in to your account and hover over the profile icon in the top right.
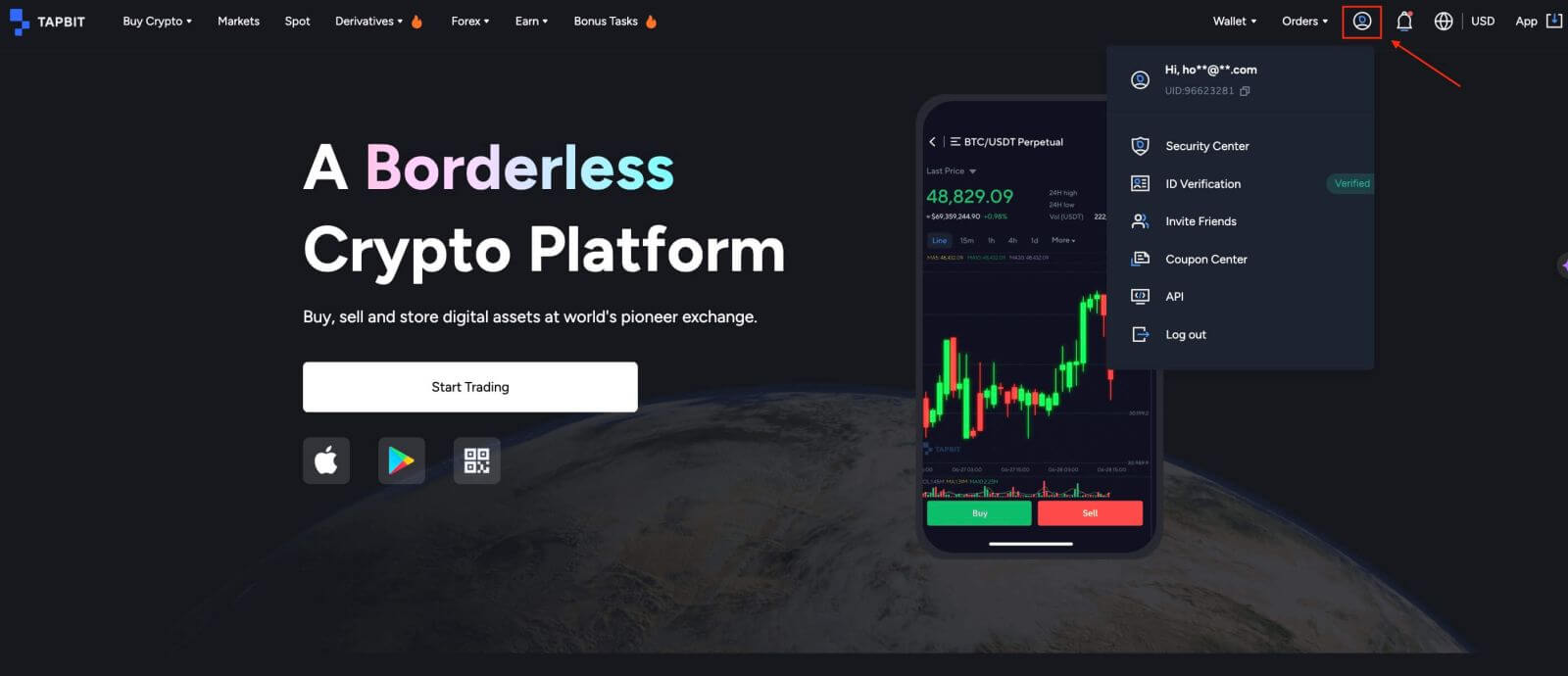
From the dropdown menu, select [Security Center] to access Tapbit’s security measures.
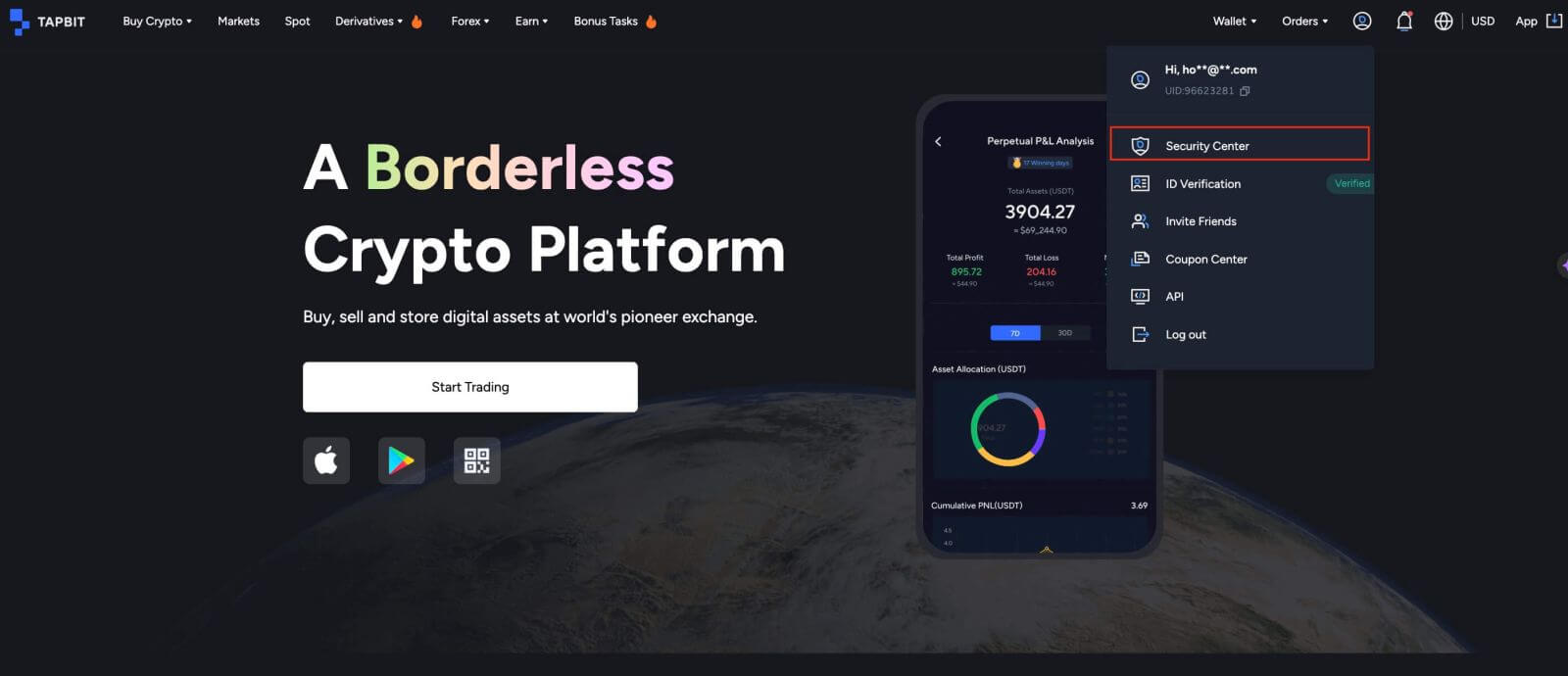
Review completed and pending security items under the [Security Center] tab.
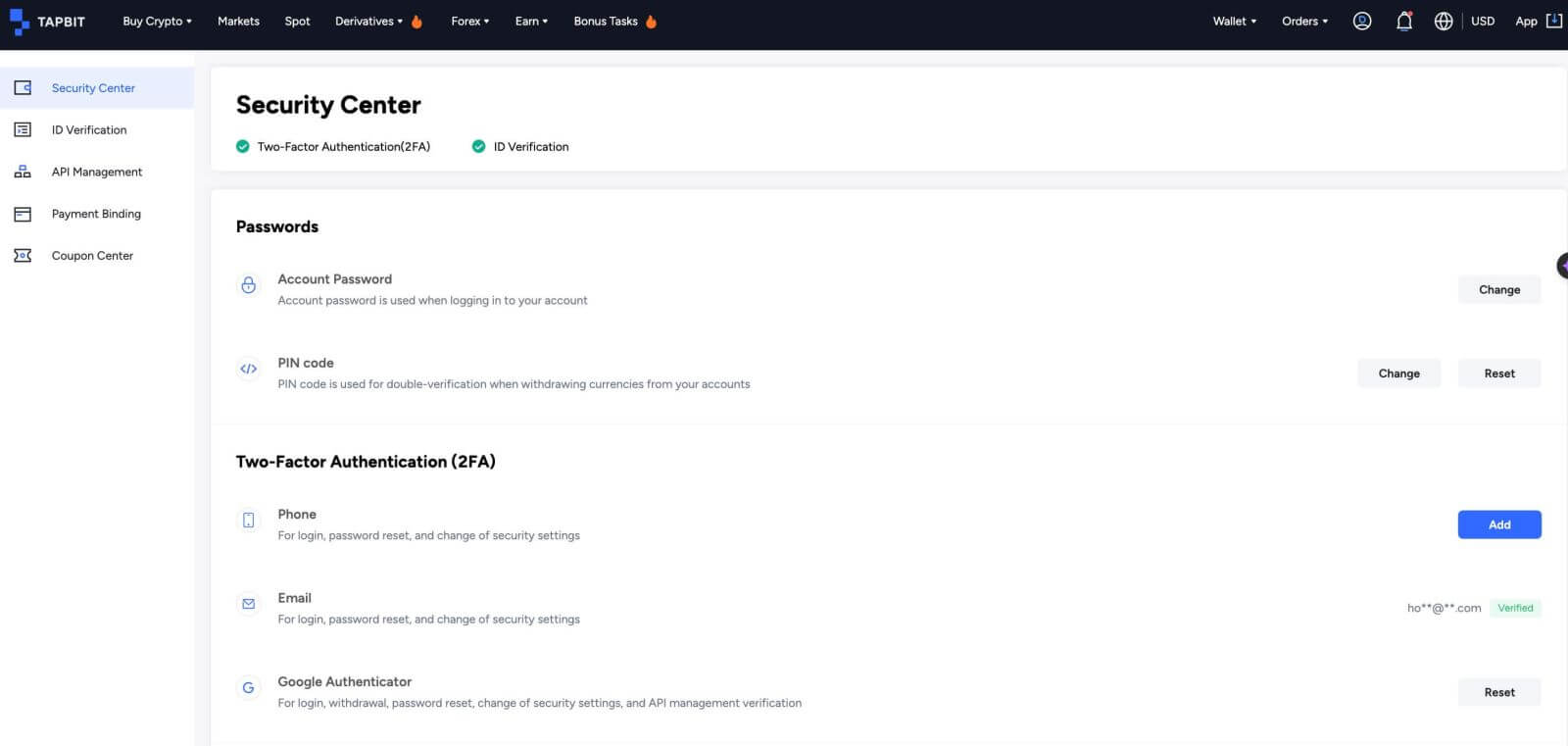
Step 3. Activate Security Features:
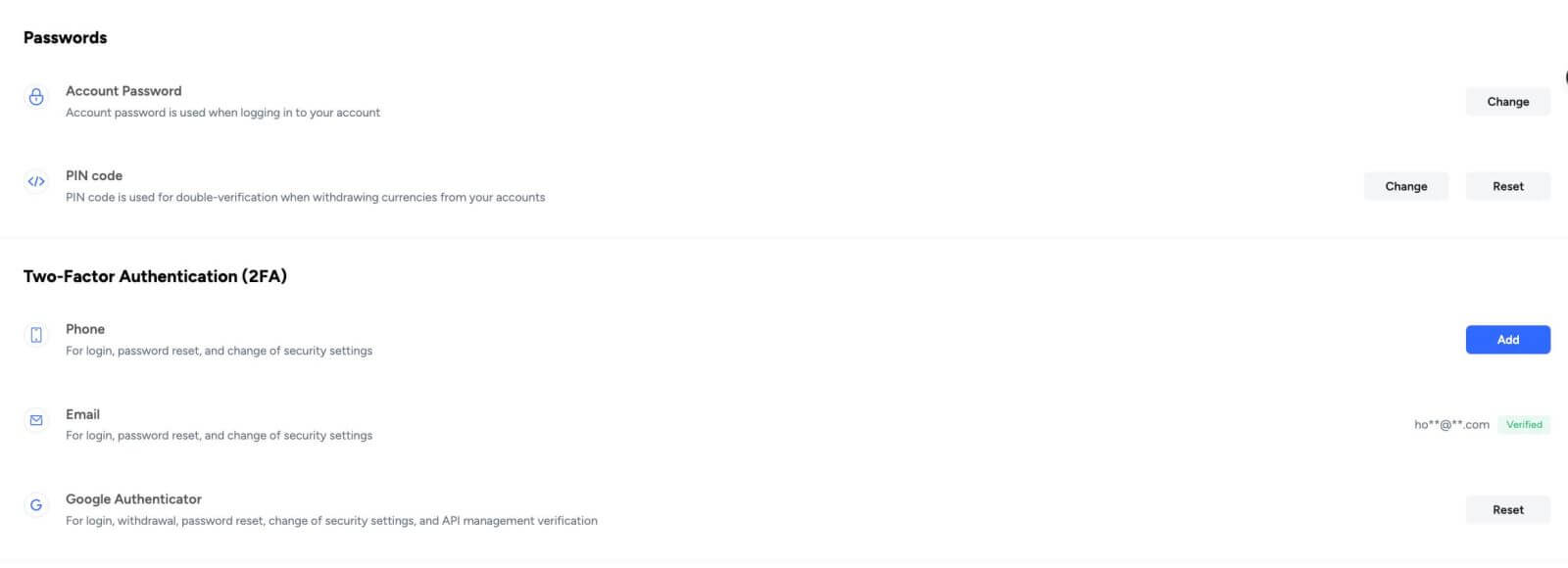
Tapbit users have the option to enhance the security of their funds by enabling different account security measures featured on the "Security Center" tab. Presently, there are five security features at users’ disposal. The initial two involve setting up an account password and completing the account verification email process mentioned earlier. The remaining three security features are detailed below.
PIN Code:
The PIN code serves as an additional layer of verification when initiating currency withdrawals from your accounts.
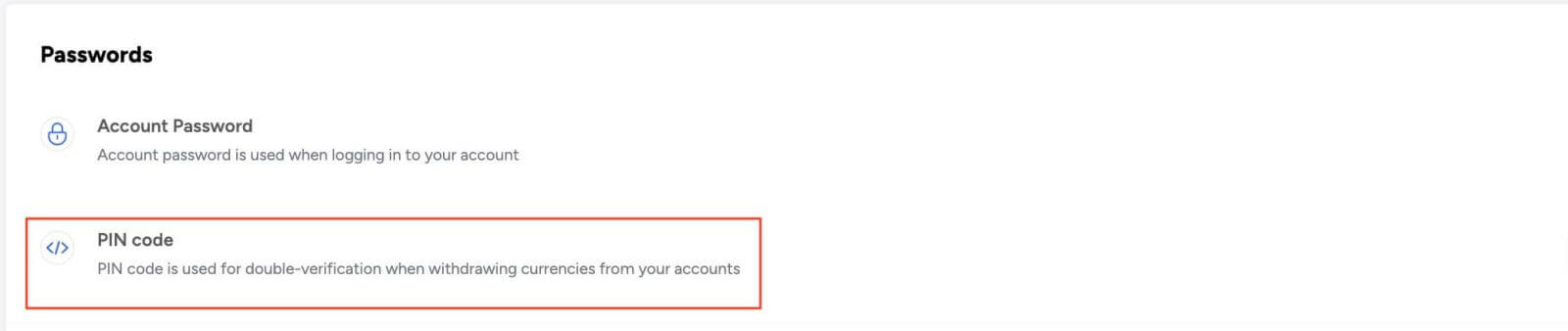
1. To activate this security feature, open the [Security Center] tab and choose [PIN code].
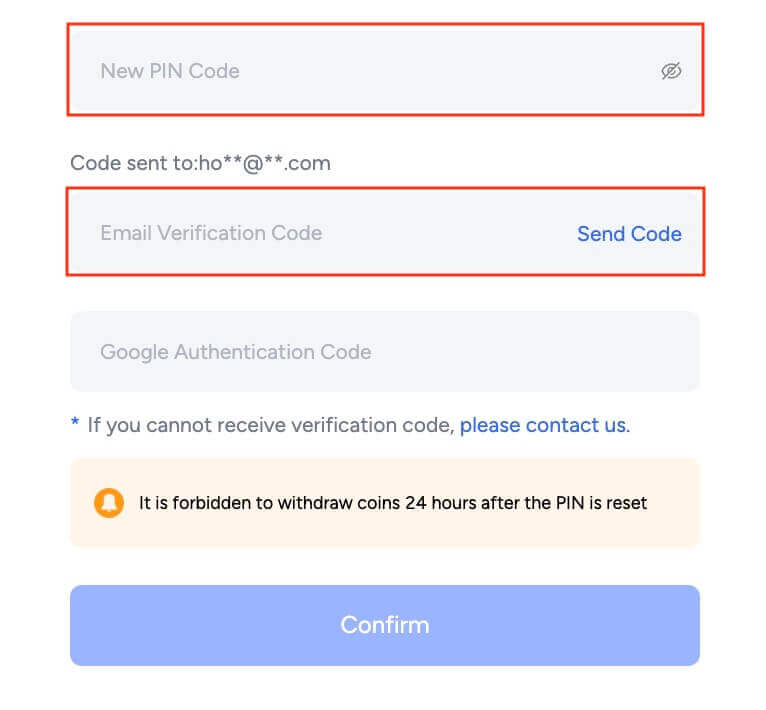
2. Click [Send Code] and check your email for the verification code, enter it in the required field then click [Confirm]
Phone Verification:
The Phone verification feature enables users to receive codes on their mobile devices, facilitating confirmation for fund withdrawals, password modifications,, and adjustments to other settings.
1. In the [Security Center] tab, click on [Add] next to [Phone].

2. Select your country, enter your mobile number, and click [Get the code] to receive SMS codes.
3. Enter the codes in the relevant fields and click [Confirm] to proceed.
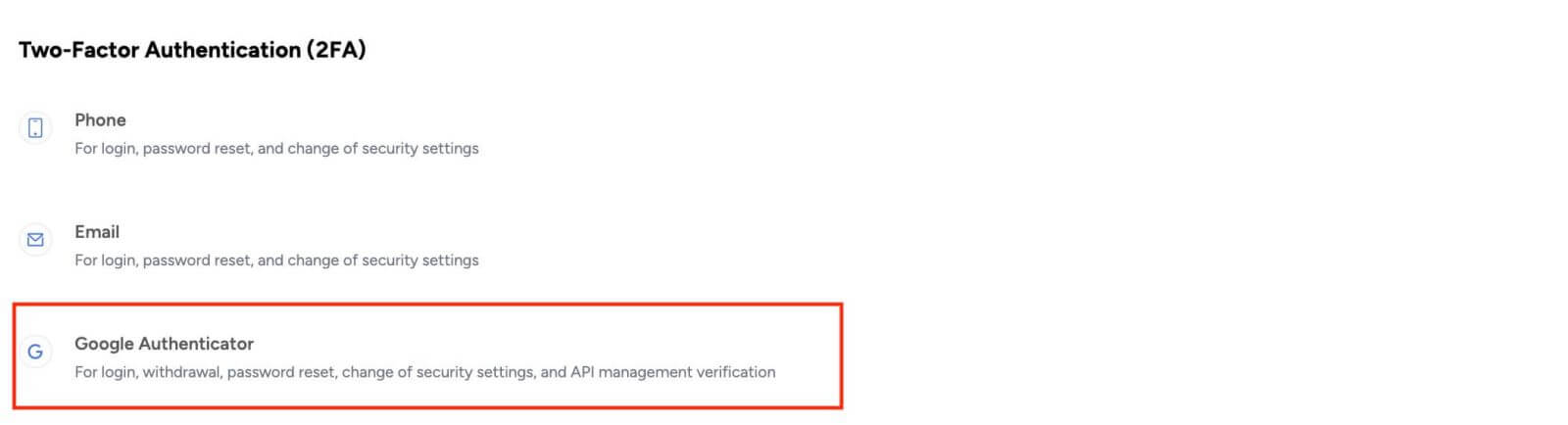
Google Authenticator:
Authenticator apps are complimentary software tools that enhance the security of online accounts. A prominent example is Google Authenticator, widely utilized for generating time-based, one-time codes. Tapbit users who enable Google Authenticator must furnish confirmation codes when withdrawing funds or modifying the security settings of their accounts.
1. In the [Security Center] tab, choose [Google Authenticator]. Users will then be directed to the webpage detailing the steps required to set up their Google Authenticator.
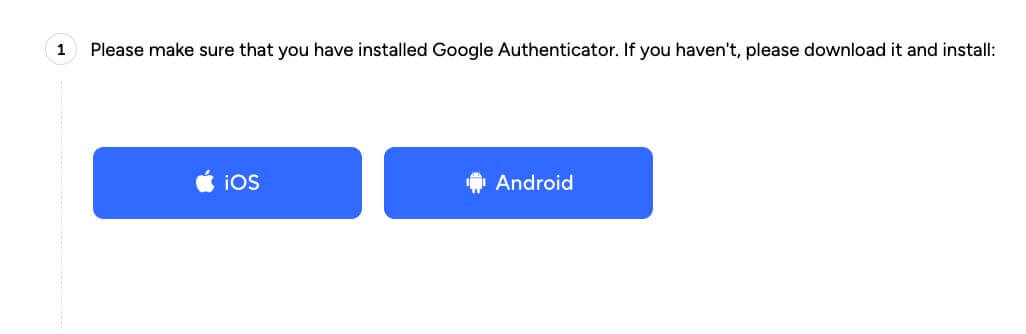
2. If you don’t have the Google Authenticator app installed, you can click the button on the webpage and download it from the Apple App Store or Google Play.
3. After installation, open Google Authenticator and scan the provided QR code or enter the provided key to retrieve a six-digit code.
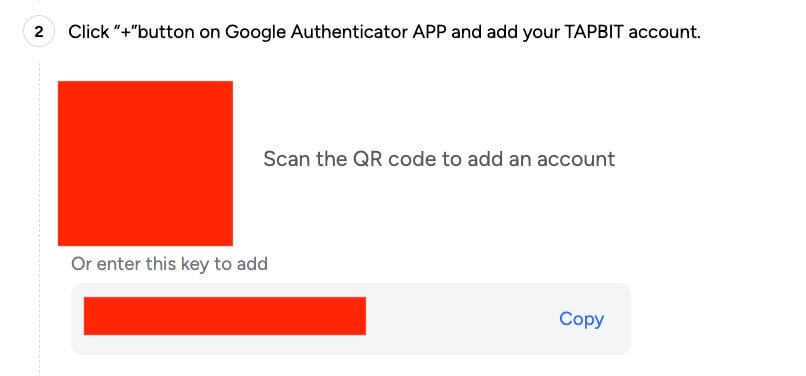
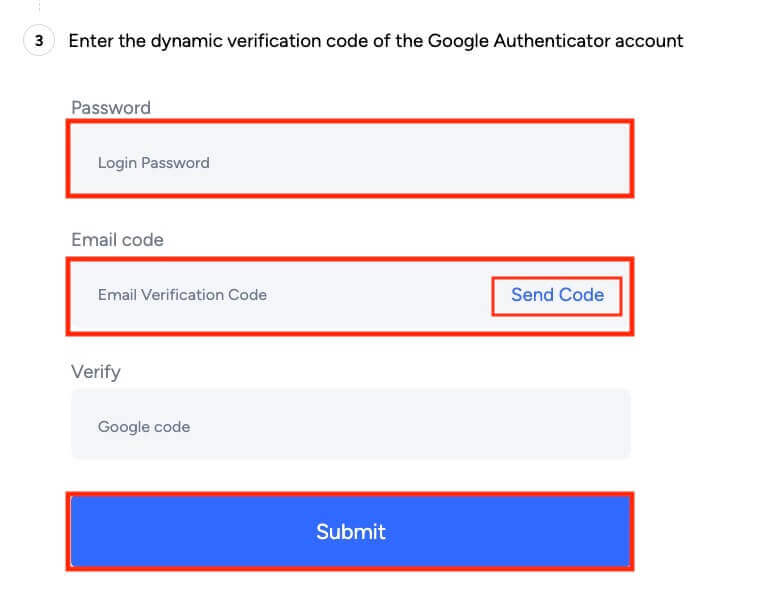
4. To complete the binding process, click [Send code] to receive a code on your email address. Enter it into the relevant field along with the six-digit Google authentication code and click [Submit] to proceed.
Step 4. Review Your Security Settings:
After configuring any security measures, locate them listed in the [Security] tab. Review and modify settings as necessary.
Note: Safeguard your digital assets by employing these security features and ensuring that your devices are devoid of malware and viruses. Such precautions are imperative given the susceptibility of digital assets to hacking and theft in the absence of a central issuing authority.
Frequently Asked Questions (FAQ)
How to prevent phishing attacks
1. Always stay vigilant when you receive:- Be cautious of deceptive emails that pose as communications from Tapbit.
- Exercise caution with deceptive URLs attempting to replicate the official Tapbit website.
- Be wary of false information in text messages containing suspicious links, urging actions like fund withdrawals, order verifications, or video verifications to safeguard against fabricated risks.
- Stay alert for false links being disseminated on social media platforms.
2. When you receive suspicious emails or messages, you should check if the email or the message is legit as soon as possible. There are 2 ways to verify:
① If you encounter any dubious text messages or emails, kindly verify them by consulting our online customer service agents. You have the option to initiate a live chat or submit a ticket, providing specific details about the issue for further assistance.
② Utilize the Tapbit Verification Search functionality for confirmation: Log in to the Tapbit website, navigate to the bottom, and select "Tapbit Verify." Input the details you wish to verify in the designated box on the "Tapbit Verify" page.
Common Scams in Cryptocurrency
In recent years, cryptocurrency scams have proliferated rapidly within the crypto world, with scammers continuously refining their methods to defraud investors. Here, we’ve identified the most prevalent fraud types:
- Phishing SMS
- Malicious software
- False promotional activities on social media
1. Smishing (Spam Text Messaging)
Smishing has become a prevalent form of fraud, where scammers impersonate individuals, official Tapbit representatives, or government authorities. They send unsolicited text messages, commonly containing links, to trick you into divulging personal information. The message might include statements like "Follow the link to complete compliance procedures and prevent your account from being frozen. (non-Tapbit domain).com." If you provide information on the fake official website, scammers can record it and gain unauthorized access to your account, potentially leading to asset withdrawals.
In case of uncertainty regarding your account, please contact us directly or verify the link through the official Tapbit verification channel.
2. Malicious software
When installing software, it’s crucial to verify the authenticity of the applications. Malicious apps can closely mimic official ones, making them appear legitimate while intending to compromise your account and assets.
To mitigate this risk, it is advised to consistently download applications from the official website. Additionally, when downloading from platforms like Apple Store or Google Play Store, verify the provider’s information to ensure the app’s legitimacy.
3. Fake promotional activities on social media
This form of fraud typically initiates with users encountering announcements on various social media platforms (such as Telegram, Twitter, etc.) promoting a sale. The promotional content often urges users to transfer ETH to a specified wallet, promising substantial returns in interest. However, once users transfer the ETH to the scammers’ wallets, they end up losing all their assets without receiving any returns. Users must remain vigilant, understanding that transactions become irreversible after withdrawals are executed.


